Google Drive is already a relatively secure platform, encrypting your data on their servers and limiting the access employees have to your Drives, with auditing for the exceedingly rare instances where an employee of Google does need to access a Drive.
Google is a massive target for hackers due to their market share, and while they’re no stranger to data breaches, as of yet, Google Drive hasn’t had a major, high-profile breach. This is great because studies show that 40% of files stored on Google Drive accounts contain some form of sensitive data that could put an organization at risk.
Threats to business data on Google Drive come from a user’s side. That means it’s your responsibility – not Google’s – to make sure it’s secure. What steps can you take to enhance your security and make sure the data stored in Drive is safe?
Classify Data
One of the greatest threats to your data security is not hackers but your own employees.
Have you ever been forced to work under seemingly asinine restrictions that don’t really matter? When you’re treating every file on your Drive as though it contains national security information, your employees are more likely to view it as an unnecessary hassle and grow lax in their habits, no matter your training and policies. After all, why would your publicly visible ad copy need to be treated the same as your financial records?
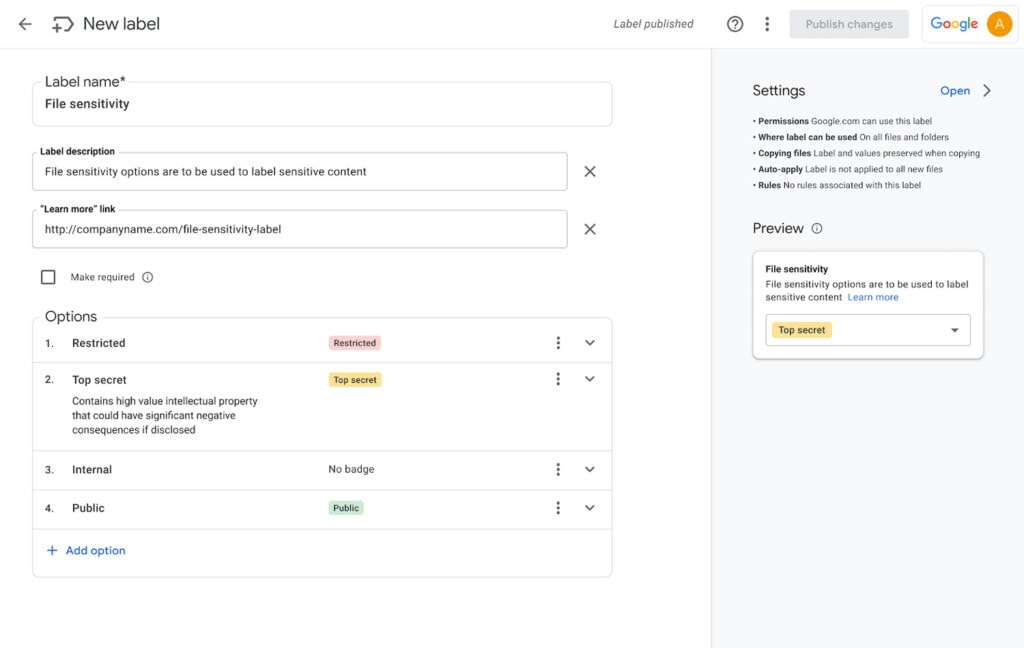
Data Classification is the practice of identifying which files in your Drive contain sensitive information and on what scale. The least important files can be treated, however, but the most important should have extra restrictions and oversight. This way, the more sensitive the information, the more respect it is given, and the less likely employees are to slip up.
Use Strong Passwords and a Password Manager
There’s a constant push and pull in user authentication. Passwords are commonplace; we all need to keep track of dozens or hundreds of them, and they all need to be strong and unique. But when a strong password looks like “Yr1+f5l0_$YA’9va”, how can you be expected to remember it, let alone remember dozens of them?
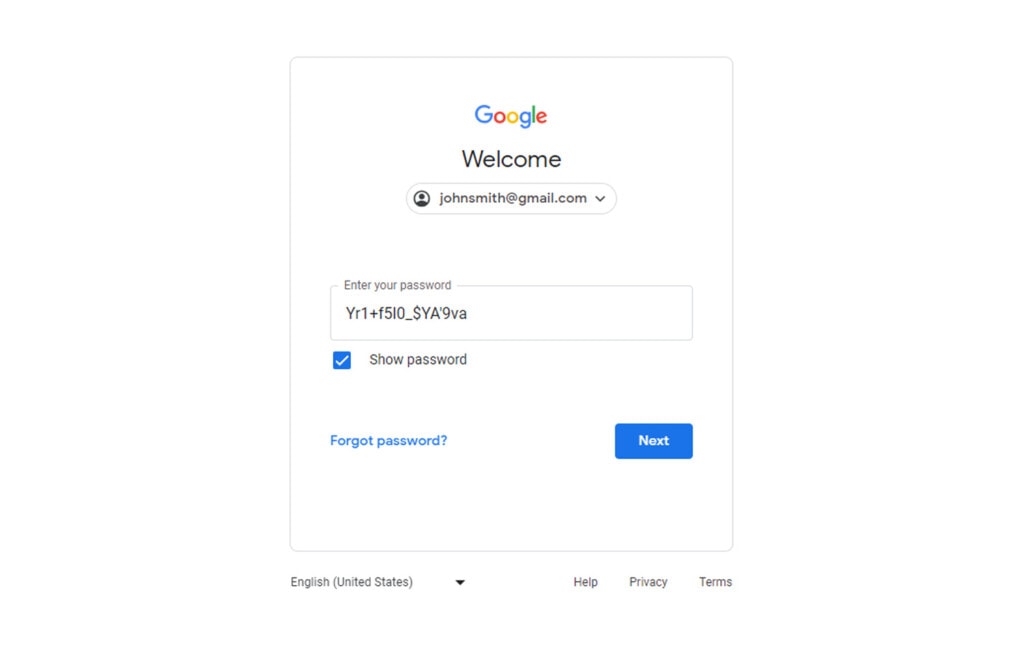
That’s where a password manager comes in. Password managers store all of your passwords and put them into websites and services for you while keeping them encrypted and secured using a master password. Using a password manager helps your employees use strong passwords rather than weaker passwords that are easier to remember.
As a side note, don’t do the 30-day password expiration thing. It encourages employees to make simpler passwords and doesn’t really help with security. Fortunately, you can use other techniques to make up for a longer vulnerability period when passwords are leaked.
Use Multi-Factor Authentication
One of the best things you can do with digital security is enforce using multi-factor authentication. Multi-factor authentication means beyond the usual username and password, Google will ask for a secondary code that is generated on the spot and rotates every few seconds. The most common way of implementing this is using Google Authenticator, but Google Drive also allows you to use other apps, as well as physical MFA tokens and other options. You can learn more about how to enable multi-factor authentication here.
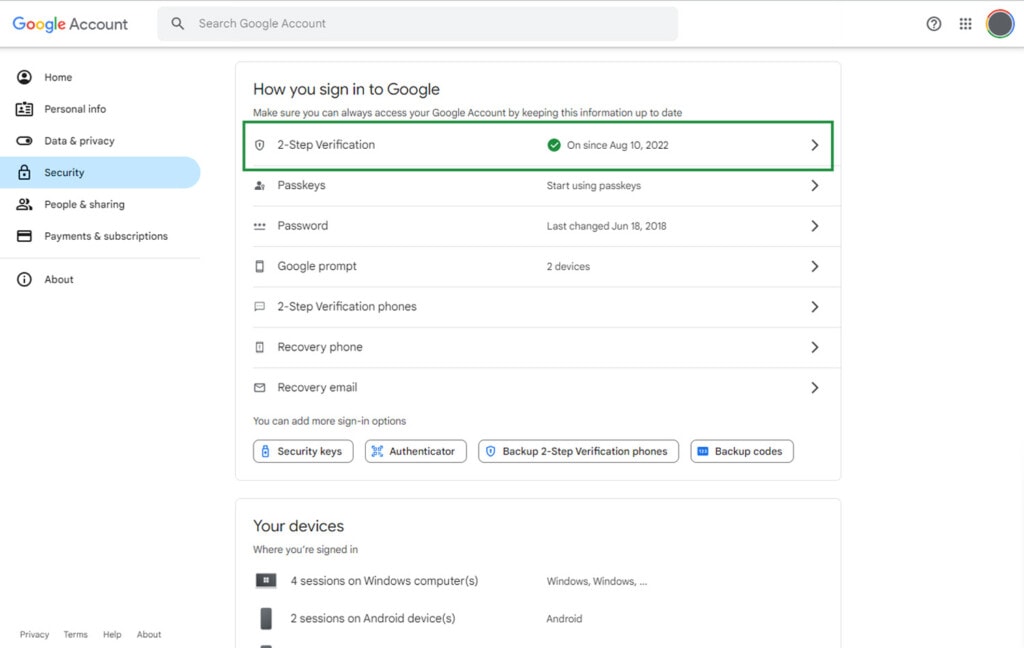
Note: Google also refers to multi-factor authentication as 2-step verification, or 2SV. They’re making it mandatory for admin accounts on workspace, which is a good thing, and it’s often a good idea to make it a policy to use company-wide. Here’s more information.
Use a Phishing Training Service
Above, I mentioned that one of the biggest threats to your security comes from your own employees. That’s true, no matter how you slice it. Unfortunately, we’ve reached a point in technological development where there are generally only three ways that a software or system is breached.
The first is through a serious exploit in the code. These happen fairly regularly and are often patched within hours or days after being discovered (and sometimes even before), but occasionally, organizations fail to update and leave themselves vulnerable. This is why keeping all of your software up to date is critical. Fortunately, with Google Drive, Google does that for you.
The second is through a supply chain attack. These are deep compromises; imagine if whoever supplied the motherboards for the servers that Google uses was installing a hidden exploit on the firmware that runs them, waiting to be triggered. These happen but are very rare and are more likely to be used to attack the government than they are your business.
The third and most common is someone in your organization receiving a message from someone they trust and clicking a link, typing in their information, sending a file, paying an invoice, grating access, or whatever else, only to later realize that sender wasn’t who they thought they were. It’s called social engineering, and it’s way easier than technical hacking these days.
There are many services that will intentionally attempt phishing campaigns against your company and provide reports of who falls for it so you can apply additional training. Work with one to help train your employees not to fall victim to social engineering attacks.
Use the Principle of Least Privilege
PLoP, or the Principle of Least Privilege, is a pretty simple concept: every individual employee, from your interns to your CEO, should have the exact amount of access to your systems that they need to do their job and no more. Believe it or not, that means your CEO probably has relatively little access, especially compared to IT, engineers, and developers.
When it comes to Google Drive, that means every individual user has the lowest level of permissions necessary. It also means they can only access the files, folders, and shared drives relevant to their job. Even if a user is compromised through phishing or hacking, this limits the potential damage they could do.
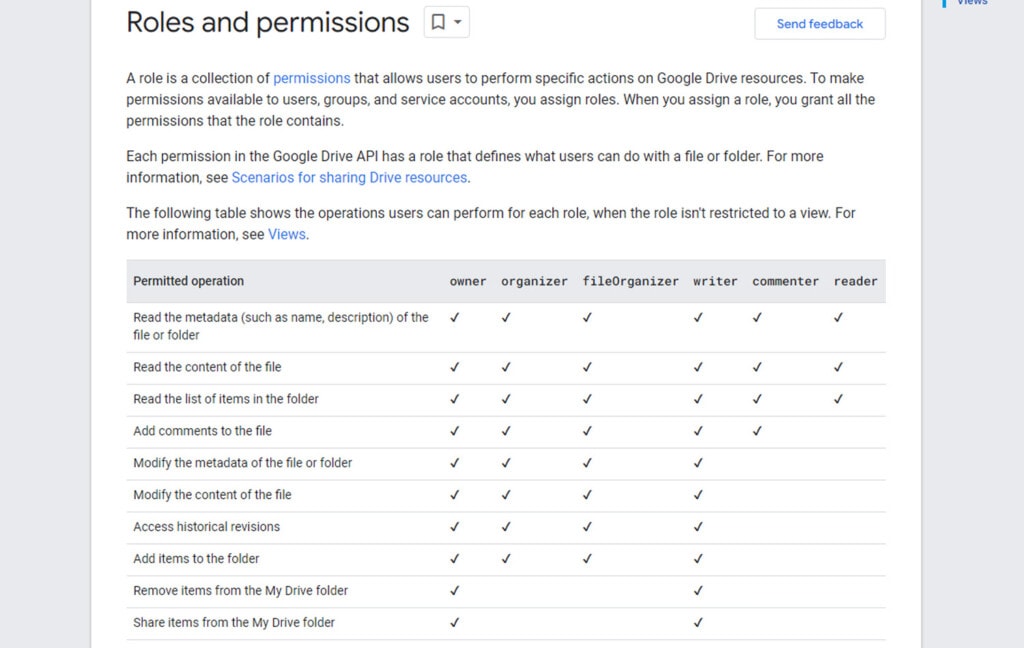
The actual organization and permissions tracking you need for this is all done manually by your IT and security teams, but the actual implementation – at least as far as your Google Workspace accounts go – is done through Google’s account management and sharing features.
Monitor File Sharing and Access
Have you ever heard the phrase “Trust, but verify”? This is where it comes into play. Your security, your policies, and your training should all be enough to keep your business information secure and out of the hands of people who might exploit it. But you can’t just trust that those policies, that training, and those security measures are all in place and working properly. You need to verify the state of things.
Auditing and tracking are the best tools for this. You need to know who has shared access to files and folders, who is granting that access, and how you can control it all.
One of the best tools at your disposal is file-sharing expiration dates. When you have a Workspace plan, and you share a file or folder with another user, you can choose what date you want that sharing to expire. This is excellent for making sure third-party users, contractors, and vendors don’t have unlimited access to files or folders in your Drive. Learn how to implement these and make it a matter of policy.
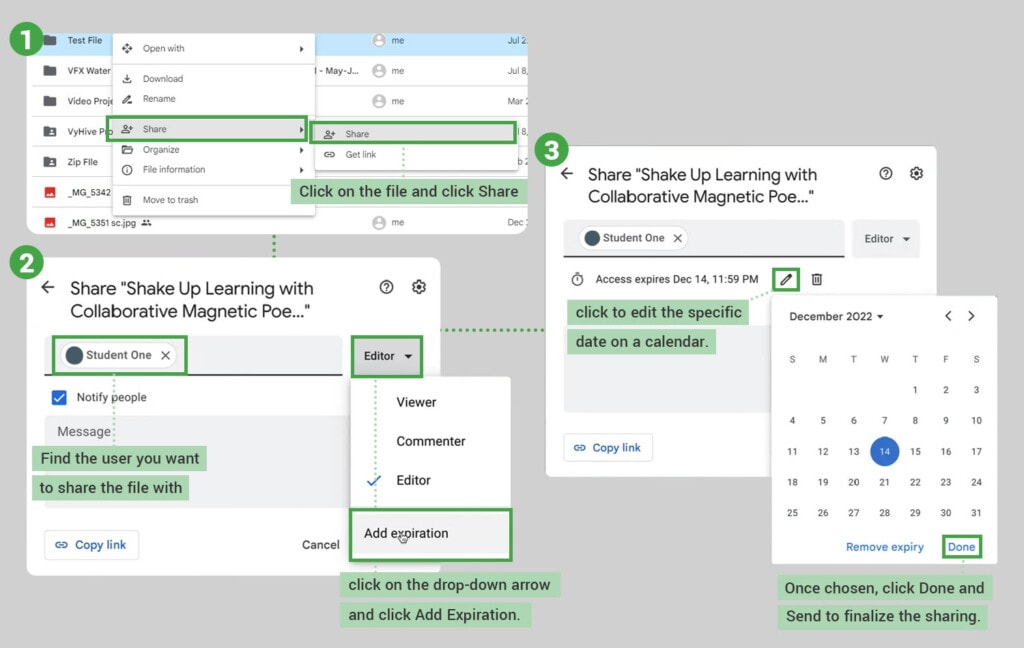
Secondly, you should periodically review who has access to what and make sure only the people who need access still have it. Sometimes, expirations don’t work for your needs, or someone does an “anyone with the link” share, or employees change roles or leave the company; in these cases, access can linger when it shouldn’t, and you need to remove it.
Use Google’s Account Recovery Features
If an employee – or worse, an administrator – loses access to their account, there can be devastating consequences. Fortunately, Google offers a few different ways to set up account recovery and backup options to restore access to the account and, if necessary, remove an intruder.
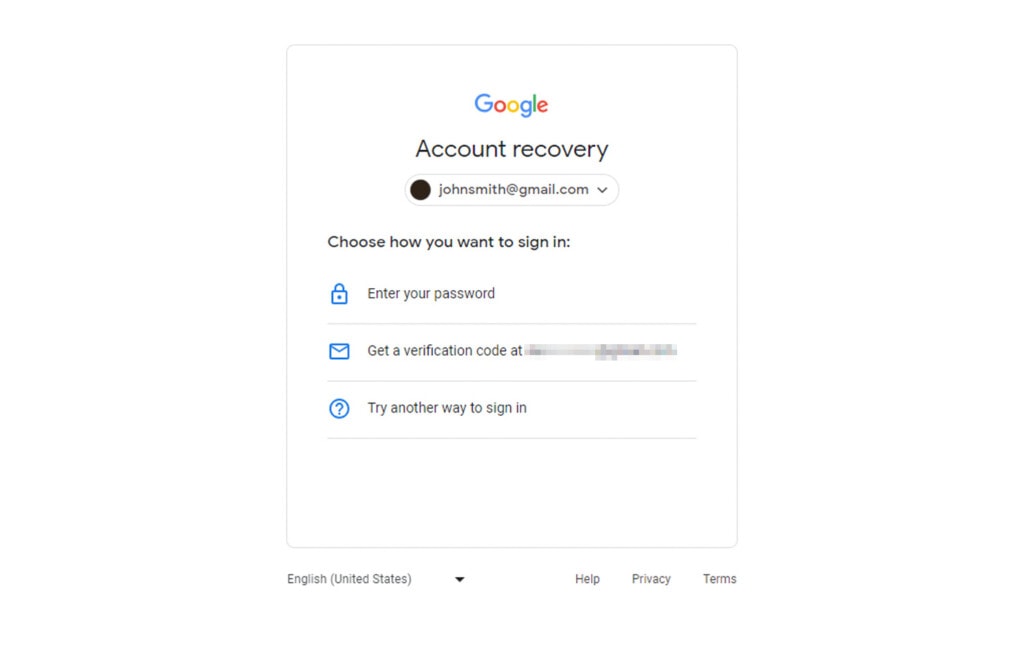
It’s worth noting that it’s much harder to do this if you don’t have account recovery set up proactively. When you have things configured properly, it’s easy to go through a process to recover an account. If you don’t, you have to jump through hoops to prove who you are. Here’s Google’s documentation and some links you can use to set up all of those backup recovery options.
Use and Maintain Off-Drive Backups
One thing some people don’t realize is that unless you have it configured very carefully, Google Drive is not a backup solution. The trouble is that Google Drive’s entire purpose is collaboration and real-time updates to files being accessed and used. That means if something happens to your files, those changes are reflected on Google Drive as well. This includes things like a cryptolocker attack or an accidental deletion.
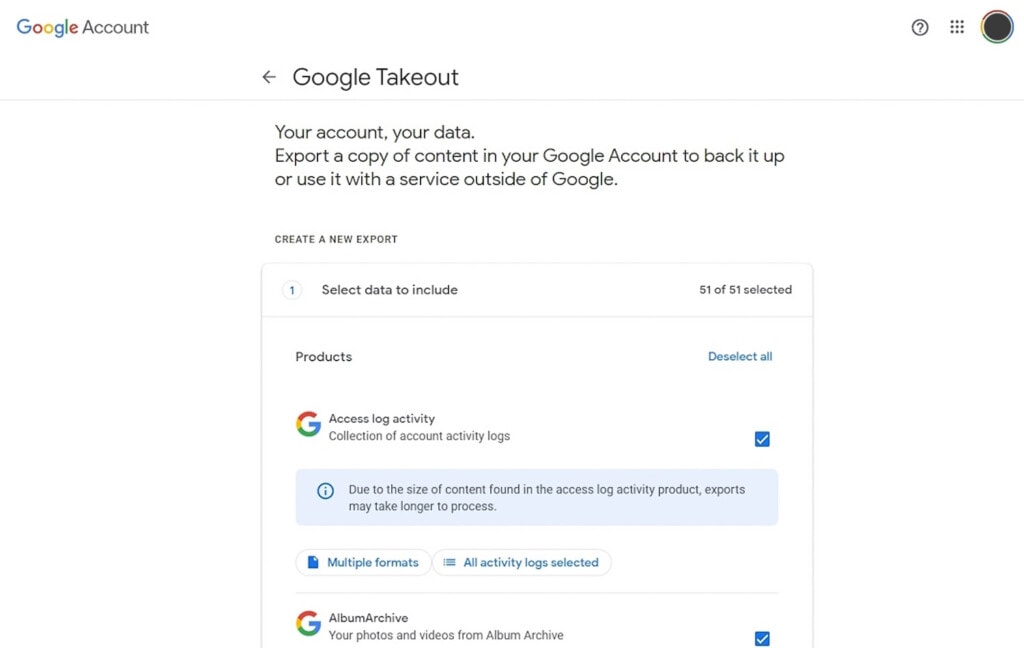
While you can use Google Drive as a backup, it’s often better to actually use a real backup solution in addition to Google Drive and use Drive for its real purpose as a collaborative tool.
Fortunately, backing up Google Drive isn’t all that difficult. I wrote a whole guide to it over here. Check it out for more information.
Use Endpoint Management
Endpoint Management is another of those enterprise-grade features that Google has available for the people who pay for Workspace accounts but aren’t available for free users. First, though, if you haven’t heard of endpoint management before, what is it?
In IT, an Endpoint is the device a user uses to access your system. Your core system is your servers and apps, and your endpoints are things like your phones, tablets, Chromebooks, and in-office PCs.
Endpoint management is a system where you can track all of those endpoints and have some manner of leverage and control over them.
So say, for example, that an employee’s car is broken into and their company laptop is stolen. Endpoint management allows you to do things like remotely locate the laptop, as well as wipe all data on it the next time it’s turned on so that even if the thief tries to access it, they can’t get into your systems.
Simpler versions of endpoint management allow you to do things like revoke authorization and require that the device log into your system via the full authentication process again, which your thief ostensibly doesn’t know how to do because they don’t have the password to the device, the multi-factor authentication key, or other details.
You can read more about Google’s endpoint management system and how to implement it here. Keep in mind that the more intrusive features like data wiping should, ideally, be limited to company-owned devices; if you use a BYOD system, use less severe revocation options.
Audit Third-Party Apps
Another semi-common vector for compromise is third-party apps, code, and permissions that are never revoked. Adding apps, whether they’re from Chrome extensions, the Google Workspace Marketplace, or phone apps, grants those apps some amount of access to your systems. This can be pretty intrusive permissions if the app has a lot of advanced features.
Google does have some level of protection here. Apps that aren’t used for some length of time have their permissions automatically revoked. However, sometimes this system doesn’t work properly, and potentially, a malicious app could keep pinging your system just to keep that connection alive. Additionally, formerly legitimate apps can be compromised.
In any case, it’s generally a good policy to perform quarterly audits – more or less, depending on the state of your company and your app usage – to determine what still has permission and what needs that permission removed.
Keep Your Drive Clean
Another way to limit any potential damage that could be done if access to your Drive is compromised is to make sure as little as possible is stored on those Drives. So, how do you know what you have, what you don’t need, and what you can remove?
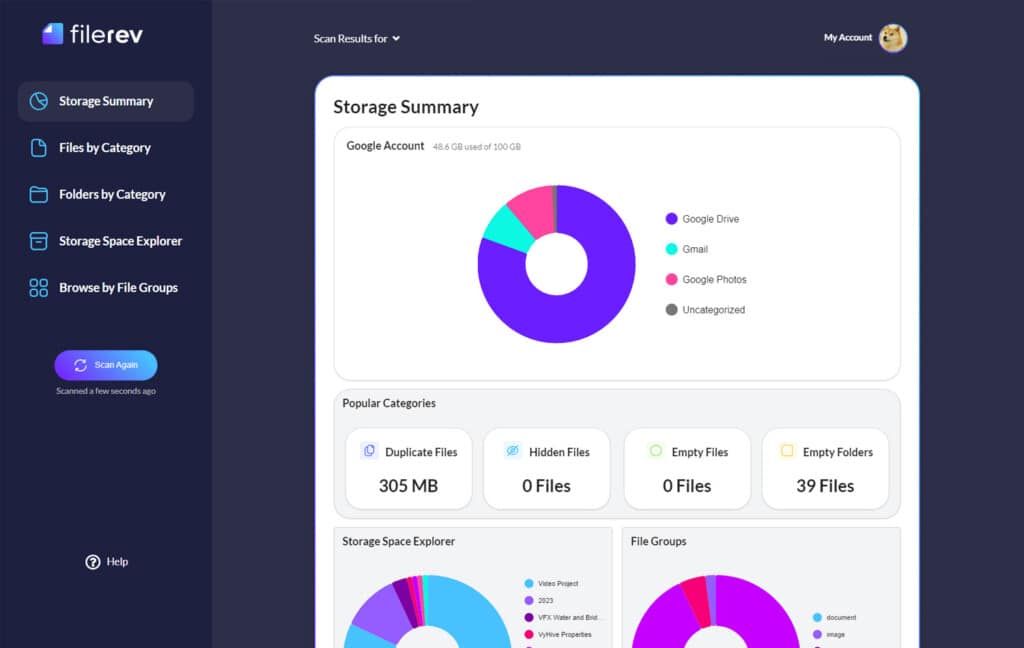
Well, Filerev can help. Filerev will scan and audit your entire Drive, giving you a report on what you have and allowing you to filter it by things like file size, age, duplication, and even hidden files you don’t even know are there. While this allows you to do handy things like free up space, it also helps you remove older, out-of-date, and unnecessary files that would nevertheless be a liability if they were to be compromised. So, why not give it a try?






Leave a Reply